Anyone who uses technology is aware of the term hacking. While a layman might have less knowledge about it than an expert, a consensus about the need to stay safe from hacking has been established. Ethical hackers make all of it possible. Thus, what you need is an ethical hacking training and certification course to become one.
There is a long list of things we can tell you about web server hacking. In this blog, we are going to get ahead by understanding more about this topic. Additionally, we will dive deeper into what is SQL injection, which is a type of cyber-attack.
Let us begin by take a better view of web server hacking. It is a vast topic and thus, we will try to cover as much as we can. However, to better understand this field in depth, you will need right training and guidance. For that, enrolling with a trust-worthy institute is a must.
Grras Solutions is a leading institute in India that offers training and certification in every top IT technology. With ethical hacking being a popular profession, especially considering the increasing dependency on the internet, this is also a course they are offering. This is your chance to begin your journey in the field.
In this blog, we will start by understanding what is web sever hacking, its types, and what steps can be taken to prevent it. Thereon, we will get to what is SQL injection, since it is one of the most common types of hacking today. So, without any further ado, let us get to it.
What is Web Server Hacking?
Web server hacking refers to attacks that target web servers. A web server is itself a computer that runs an operating system. It is connected to the backend database and runs numerous applications. If there is any sort of vulnerability in the database, network, operating system, or the application, it will become open to the possibility of an attack.
Unless we talk specifically about ethical hacking, web server hacking comes under the tag of a malicious attempt. It is done with the purpose of gain unauthorised access to that server. There are various reasons with which this act could be carried out including gaining control of the server, disrupting the services, or stealing data.
This criminal offense is a serious threat to businesses everywhere. It leads to financial losses, reputational damage, and data breaches.
It is a type of cyber-attack focused on targeting web servers. There are various kinds of web server hacking, of which SQ injection is one. Other names include brute force attacks and cross-site scripting. Before we get into details about this attack, let us see how such hacking acts can be prevented.
Of course, there is no hundred percent guarantee that your organization will stay safe, but trying is must.
Tips to Prevent Web Server Hacking
There are many steps you can take as an ethical hacker to ensure your organization is safe from all external threats. Your ethical hacking and cybersecurity training course will give you all the knowledge you need to make it happen.
With an institute like Grras Solutions, you will also be able to gain the right skills to make it happen. This place offers you the opportunity to work on live projects, rendering you with practical skills and abilities. Thus, you will have a better idea about what you are doing when you step into the real-world.
Here are some of the best steps you can take to ensure your web server is safe.
1. Implement Strong Passwords
One of the key things to keep in mind is implementing strong passwords. There are various conditions you can set while doing so such as keeping the password as 8 character long, having both upper case and lower case, having a special character and number, etc.
You should also avoid using common names or knowledge that others know about you. Regularly changing passwords is also important.
2. Use Firewalls and Intrusion Detection Systems
Using firewalls and intrusion detection systems aid in detecting and blocking malicious traffic effectively. Firewalls block traffic from malicious IP addresses that are already known. Intrusion detection system, on the other hand, detects suspicious activities on the server.
Both these systems can be configured to send alerts to administrators in case any suspicious activity is detected. Thus, quick actions can be taken.
3. Use Secure Protocols
There are various secure protocols that can be used for the protection of the data that gets transmitted between the clients and the web servers. Some commonly used ones are SSL/TLS. The protocols encrypt the data that renders it difficult for the attackers to intercept it.
4. Use Two-Factor Authentication
If you are looking to add an additional later of security to protect an organization from web server hackers, then you should use two-factor authentication. This incorporates the user to give two pieces of information to gain any sort of access.
There are various things and combinations you can follow to carry out this tip.
5. Monitor the Server Regularly
Another important step in keeping hackers off your web server is to regularly monitor the server. Administrators should look for all sorts of suspicious activities. This include unauthorized access attempts and unusual traffic patterns.
Monitoring the server regularly will also aid in finding any software vulnerabilities that could have otherwise been exploited by the attackers.
Now that you have a basic idea about web server hacking and how you can prevent it, it is time to move on. In the next segment of the blog, we are going to give you a brief about SQL injection. Let us explore what it is.
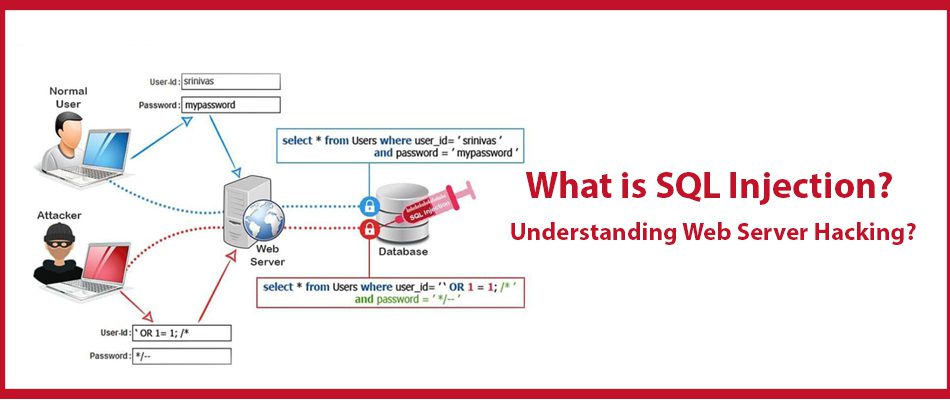
What is SQL Injection?
SQL Injection, also known as SQLi is a kind of an injection attack. This gives attackers the window to execute malicious SQL statements. Such statements regulator a database server at the back of a web application.
SQLi vulnerabilities are used by the attackers to overcome any application security measures. This includes going around the authorization and the authentication of the web application or the web page. This action allows them to retrieve all the data of the SQL database.
An injection attack incorporates various attack vectors. In such an attack, the attacker adds untrusted input inside a program. Consequently, this input is processed as a part of the query or the command by the interpreter. Thus, altering the execution of the said program.
An injection attack is one of the major problems that arise in web security. It is one of the oldest as well as the most dangerous attacks on web applications.
Such a vulnerability holds the potential to attack any web application or website using an SQL database. This includes Oracle, MySQL, SQL Server, etc. Criminals can gain access to sensitive data such as intellectual property, personal data, customer information, trade secrets, and more.
How to Prevent SQL Injections?
It is not easy to prevent an SQL injection. There is a reason why it was at the top of the list by the OWASP organization for being a grave threat to web application security.
However, it does not mean that we do not take any steps. Prevention is better than cure and thus, as a cybersecurity expert, it is going to be your duty to implement all the right measures to make it happen. Here are some steps you can undertake to ensure you have done everything you can to prevent SQLi.
- Train and Maintain Awareness – everyone who is a part of building the web application process much have knowledge about the risks linked with SQLi. Suitable training accordingly is thus essential.
- Do not Trust any User Input – it is advised to treat every user input as untrusted. This is because a clever attacker can find different ways of making it happen.
- Use Whitelists – try to verify and filter all user inputs using whitelists strictly.
- Adopt Latest Technologies – SQLi protection is not found in older we development technologies. Thus, you should use the latest technologies and even keep revising them with time.
- Employ Verified Mechanisms – while you might want to, but we advise you not to build your SQL injection protection from scratch. Use verified mechanisms that already offer protection again SQLi.
- Scan Regularly – there are many ways in which SQLi may be introduced in the system. regular scanning will help you find them and start amending as soon as possible.
Conclusion
Web server hacking comes under the tag of serious threats to any business. Thus, it is essential to stay alert and protected from them. SQLi is one of the most harmful attacks that can damage the entire internals of an organization.
You can become someone who helps companies stay safe and secure with training and certification. Become a cybersecurity professional with Grras Solutions and get introduced to the world that needs your prowess. Enroll with the right course now and start your journey in this field today.








 Whatsapp us
Whatsapp us Call us
Call us





